Variable Overwrite
Now, we will do a slight variation on a similar challenge. Now, we need to change the data to a specific value. Let's look at the challenge description:
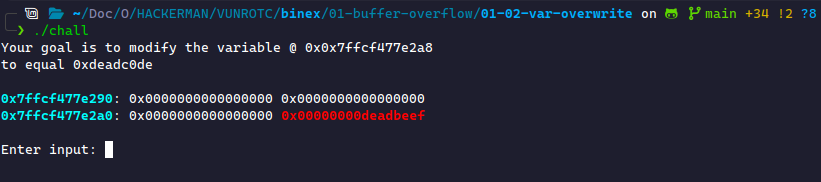
Our padding is identical. Instead of overwriting the Red block with random data, we must fill it with something meaningful.
We can see that the padding will be the same as the last challenge. Ensure you understand how to compute that padding, even without the challenge providing the visualization. Instead of filling that block with random characters, like B, we must fill it with 0xdeadc0de. If we try filling this, it doesn't quite work:
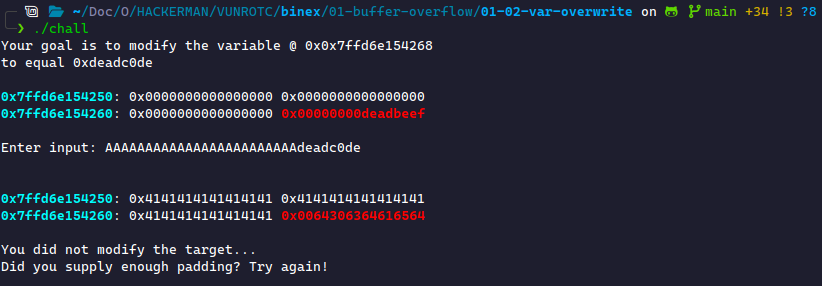
Why doesn't the data show deadc0de? This is because the data is read in as characters rather than hexadecimal. We can throw this block into a program like CyberChef to see it:
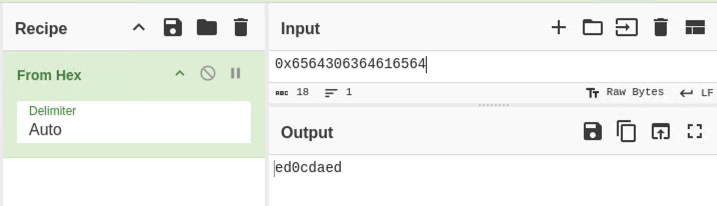
This tells us we must send the data as bytes to the binary. If we put in 0xdeadc0de into Cyberchef, we see it prints nonsense:
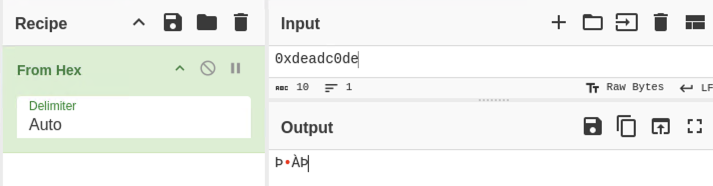
This is because most of these characters aren't on the ASCII table! The ASCII table only supports up to 0x7F, so these print as random characters.
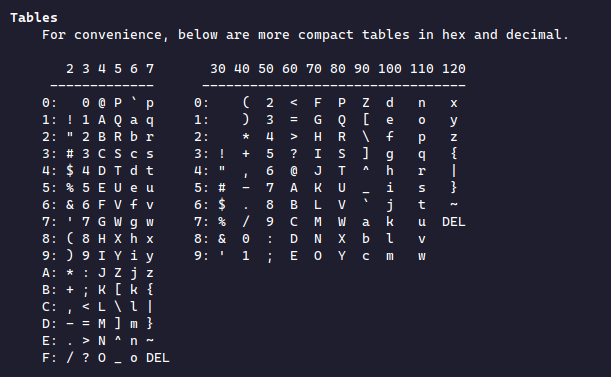
Therefore, we can't abuse this using a plaintext input. We need something else to print these bytes and pass them to the binary. We'll use echo for the sake of simplicity. The -e flag will evaluate bytes and return their "ASCII equivalent". Let's pack these up and send them:
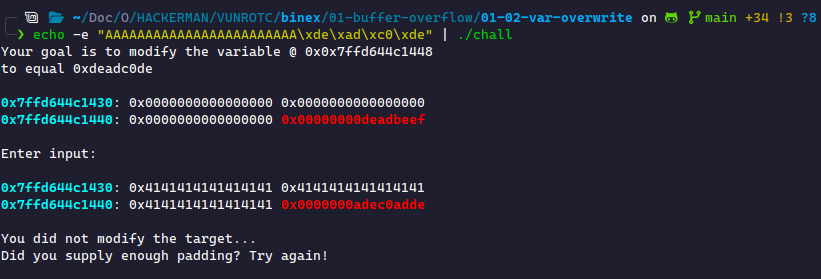
With this input, we notice two major problems:
- The bytes are printing backward from the way we inputted them. This is directly related to why Cyberchef printed our string backward.
- There's an extra
0x0abyte at the end of our input! Referencing the ASCII table, this is the newline character:
012 10 0A LF '\n' (new line)
We can fix the second problem using the -n flag for echo, which doesn't include a newline character in the output. Now, let's discuss the first issue.
Nearly all executables are written as LSB (Least Significant Byte) binaries. This means that when the binary reads a block (8 bytes on the stack), it reads the least significant byte first. This is backward from how humans read, who read in MSB (Most Significant Byte). To us, the binary reads from right to left, causing our input to be read backward. To fix this, we need to pack our input backward.
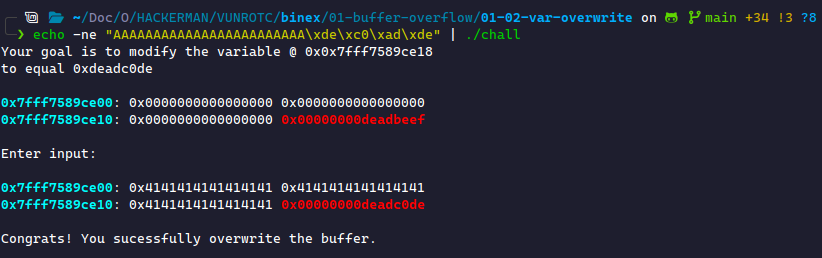
Once we make these two fixes, we get a successful overwrite!